
How Long Can A Pokemon Stay In A Gym, How long can a Pokemon stay in a gym without berries, 1.26 MB, 00:55, 640, Ask About SPORTS, 2020-08-07T21:37:34.000000Z, 19, How long can a pokemon stay on a gym? | Pokemon GO Wiki - GamePress, pokemongo.gamepress.gg, 1440 x 1280, png, pokemon gym stay gamepress pokemongo, 20, how-long-can-a-pokemon-stay-in-a-gym, KAMPION
A) the key is made up of two integers, each of which must be between 0 and 25. B) the operations performed by the encryption and decryption functions are done using arithmetic modulus 26. C) the first element of the key must be relatively prime to 26. D) an affine cipher is effective against a brute force attack.
(choose all that apply. ) a. Pseudorandom number generators b. Which of the following is a reason that ipsec has become the standard protocol for. In tunnel mode, encapsulating security payload encrypts which of the following? It’s used by cryptographic designers as their most basic building blocks. These building blocks are a part of a cryptosystem, which is a suite of cryptographic algorithms needed to implement a particular. Cryptographic primitives are the basic building blocks of a security protocol or system. In the following section, you are introduced to cryptographic algorithms that are essential for building secure protocols and systems. A security protocol is a set of steps taken to achieve the required security goals by utilizing appropriate security.
Which of the following is true about ACLs on Cisco routers there is an

ZeroPool | Devpost

ZeroPool | Devpost

ZeroPool | Devpost

ZeroPool | Devpost

ZeroPool | Devpost

Generating a Bitcoin Address From One Word

Merkle-Damgård Length Extensions and Keccak256 – Aftermath.digital
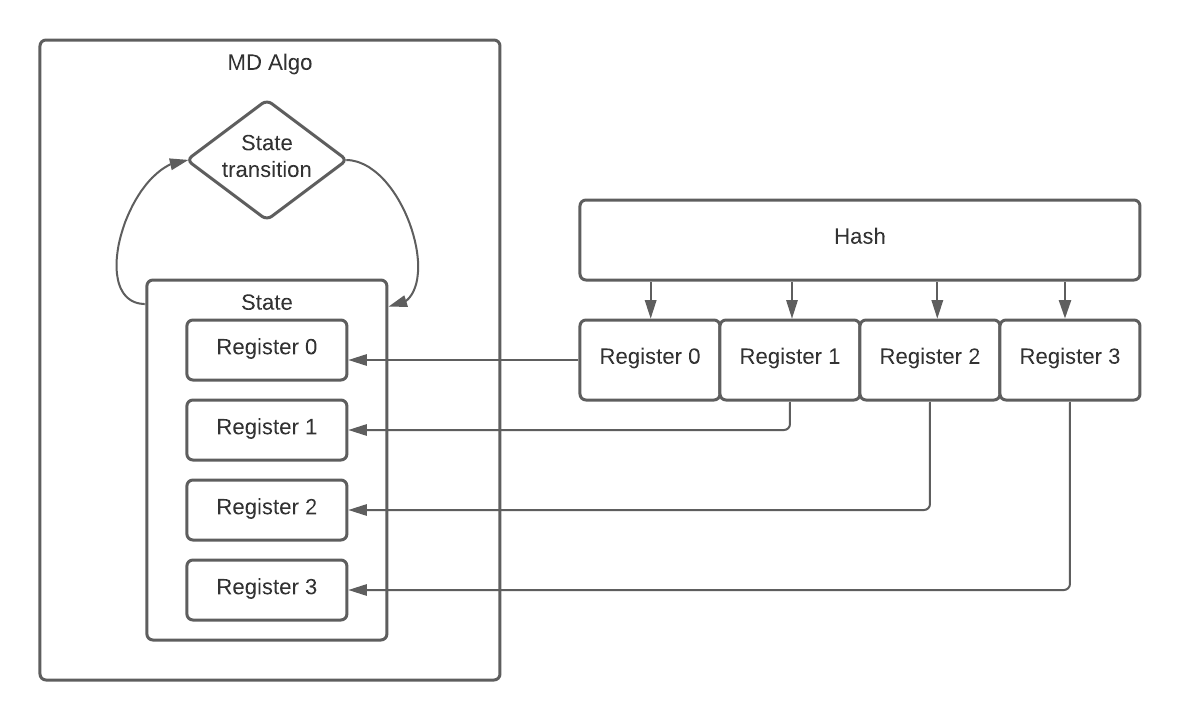
ZeroPool | Devpost

ZeroPool | Devpost

EmoticonEmoticon